A security vulnerability was discovered at GitHub this week that made it possible for an attacker to add new SSH keys to arbitrary GitHub user accounts. Although there was no known malicious activity using this exploit, they are taking the responsible step to email all their users that have SSH keys associated with their account to verify and approve them before they can be used to clone/pull/push repositories over SSH.
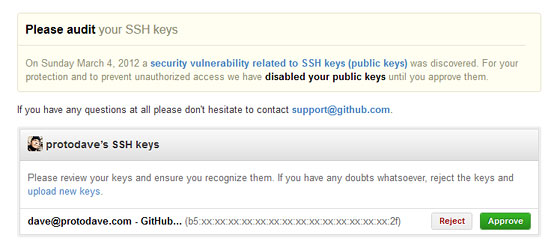
The GitHub audit page looks like this:
Here’s a quick reminder of how to get the fingerprint of your SSH public key using the ‘ssh-keygen’ command. Use the name of your local public key file that you want to check.
ssh-keygen -lf id_protodave_github.pub
The resulting fingerprint will look like:
2048 b5:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:xx:2f protodave@github (RSA)
If this fingerprint of the local trusted copy of your SSH public key matches the one GitHub shows you, then you are safe to click “Approve”.